Intro
A Not So Very Intelligent Fuzzer
Contact: marshallwhittaker@gmail.com
If you perfer group discussions, please join ##ansvif on the Freenode IRC network!
As the complexity of a system rises, as does the potential for problems within that system.
--Whittaker's Law
The fuzzer ansvif is designed to find code bugs by throwing garbage input at programs to see how they react. This is great for finding bugs, because not every type of input is always handled, and buffers are not always checked, etc. It also comes in handy when writing (and protecting against), buffer overflow exploitation, as well as string format vulnerabilities (the %s bug). For more information, visit the Wiki on GitHub.
Checkout and compliation
$ git clone https://github.com/oxagast/ansvif
$ cd ansvif
$ aclocal
$ autoconf
$ automake -a
$ ./configure (or) $ ./configure --enable-gtk
$ make
$ make check
README
# ansvif
A Not So Very Intelligent Fuzzer.
Compliation:
Dependancies:
automake autoconf-archive zlib1g-dev g++ gcc crypto++ (and libgtk2.0-dev if you want the GUI)
Linux:
$ aclocal && autoconf && automake -a && ./configure && make && make check
or
$ aclocal && autoconf && automake -a && ./configure --enable-gtk && make && make check
OpenBSD:
$ CXX=$(find / -name 'eg++' 2>/dev/null | grep ports | head -n 1) AUTOCONF_VERSION=2.69 \
AUTOMAKE_VERSION=1.15 autoreconf -fmi
$ make check
Windows:
Now Windows code is designed to be compiled with MinGW-W64.
$ ./configure_win
$ make
If you would like to try out the example code, you can compile faulty.c with:
$ gcc faulty.c -o faulty
Using the example code:
You can point the memory back at address \xff\x05\x40\x00\x00\x00\x00\x00 (the
subroutine containing the code that spawns bash) with:
$ ./buffer_overflow -a $(perl -e 'print "A"x24;print "\x00\xff\x05\x40\x00\x00\x00\x00\x00"')
The address may be a little different under your distro, check gdb if you really
want to try it out. The code above /should/ drop you at a bash prompt.
If the code is set to a mode where all are able to execute as another user, it will
attempt to spawn a root shell.
Please note that the example faulty buffer_overflow when compiled under Debian 9 does
not throw an error detectable by ansvif when you fill it with trash.
Ex:
$ ./buffer_overflow A AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
returns 1 with:
$ echo $?
This as far as I know is a Debian specific bug.
Useage:
Important note: Windows users will have to run ansvif.exe from Powershell for it to work!
$ ./tools/find_suid.sh /usr/bin/ /bin/ /sbin/
# ./tools/bermise_fuzz.sh nc 127.0.0.1 22 (should be run as root or be able to read /var/log/syslog)
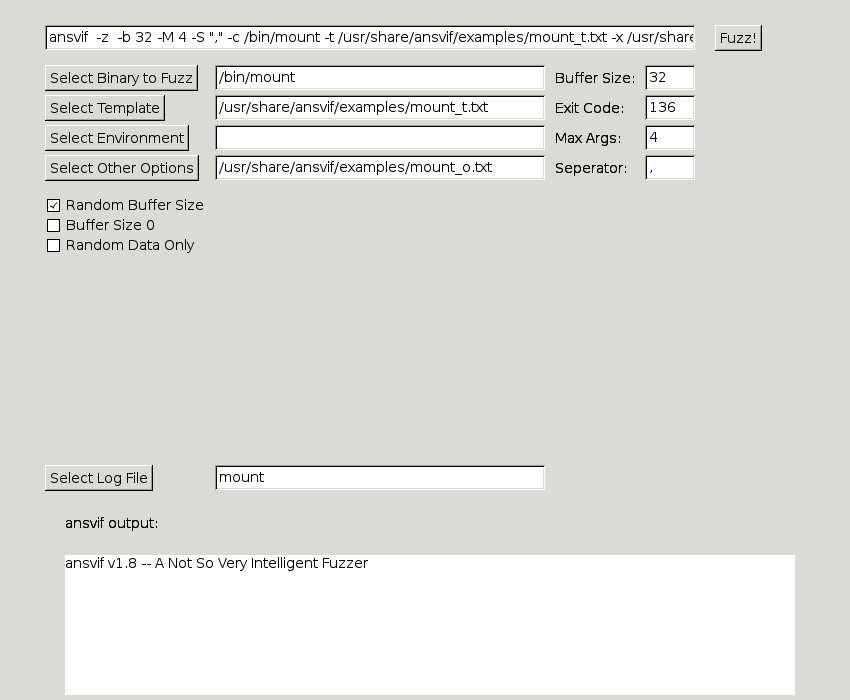
$ ./ansvif -[tm] [template/manpage] -c /path/to/executable -b buffersize
$ ./ansvif_gtk -l
$ ./ansvif_gtk -p /usr/bin/ansvif_gtk
Examples:
Linux/BSD:
Fuzzing /bin/mount (a suid 0 process) example:
$ ./ansvif -m mount -c /bin/mount -e examples/mount_e.txt -x examples/mount_o.txt\
-f 8 -b 2048
Iceweasel (Firefox) fuzzing example:
$ ./ansvif -t examples/blank.txt -F tmp/tmphtml -x examples/htmltags.txt -c /usr/bin/iceweasel -b\
128 -A "file:///home/username/src/ansvif/tmp/tmphtml" -f 2 -n -R "sleep 3 && killall\
iceweasel" -S ">"
Syscall fuzzing example:
$ cat examples/linux_syscalls_implemented.list | xargs -P \
`cat examples/linux_syscalls_implemented.list | wc -l` -I {calls} ./ansvif -t examples/space.txt \
-B "{calls} " -c ./syscalls -o syscall_crash -f 1 -z -d -b 16
Windows:
Google Chrome fuzzing example:
PS C:\ansvif\bin\ansvif_win> .\ansvif -t ..\..\examples\space -F ..\..\tmp\tmphtml -x `
..\..\examples\htmltags -c `
'C:\Program Files (x86)\Google\Chrome\Application\chrome.exe' `
-b 128 -A "file:///C:\\Users\marsh\OneDrive\Documents\Code\ansvif\tmp\tmphtml" `
-f 2 -n -S ">" -R "sleep 2 ; Stop-Process -Name chrome"
Options:
-t This file should hold line by line command arguments as shown in the example file.
-e This file should hold line by line environment variables as shown in the example
file. You can usually get these by doing something like:
$ strings /bin/mount | perl -ne 'print if /[A-Z]=$/' > mount_envs
-c Specifies the command path.
-p Specifies the manpage location (as an integer, usually 1 or 8)
-m Specifies the commands manpage.
-D Dumps whats found in the manpage.
-f Number of threads to use. Default is 2.
-b Specifies the buffer size to fuzz with. 256-2048 Is usually sufficient.
-r Uses only random garbage data.
-o Writes output to log file.
-z Randomize the buffer size from 1 to what is specified by -b.
-x Other junk to put in. Usernames and such can go here.
-S Seperator between options.
-s Omitted character specification. Defaults are <>\\n |&\[]\()\{}:;\ and newline is mandatory.
-T Timeout for threads.
-W Timeout for threads.
-L Unpriviledged user to run as if root.
-A Always put whats after this after command to run.
-B Always put whats after this before the command to run.
-F File to feed into the program that -x along with normal fuzzing data will be put in.
-n Never use random data in the fuzz.
-R Run this command after each fuzz.
-C A Non standard error code to detect.
-V Use Valgrind if installed.
-1 Try to make it fault once, if it doesn't happen, throw error code 64. Useful for scripting.
-P Use % to represent binary in fuzz.
-M Max arguments to use in the fuzz.
-y Short for -b 0 and usually only useful with -A or -B.
-K Keep going after a crash.
-E A command to be run before the fuzzed program.
-0 No NULL characters in the fuzz.
-v Verbose.
-d Debug data.
-h Shows the help page.
Recommendations:
DO NOT RUN THIS CODE IN A PRODUCTION ENVIRONMENT!
If you try setting faulty.c's output to suid(0) then PLEASE do it in a virtual machine.
or atleast a machine that you don't care about.
Other than that, just play around and have fun!
Notes:
Windows users must have ansvif running from Powershell.
Linux and Windows code should be relatively stable.
Other
It can be interesting to run things through progarms like radamsa and pipe their output into ansvif.
Syscall fuzzing is only about 20% complete at this time, so it's not ready for use.
Authors and Contributors
Marshall Whittaker (@oxagast), with some help from other sources such as stackexchanges, IRC, and dll999 for syscall fuzzing ideas. Thanks!
Support or Contact
You can contact me at marshallwhittaker@gmail.com and I will try to respond in a timely manner!